A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
What is vulnerability assessment
Types of Vulnerability Assessment
Host-based assessment
Used to locate and identify vulnerabilities in servers, workstations, and other network hosts. This scan typically examines open ports and services and can offer visibility into the configuration settings and patch management of scanned systems.
Network and wireless assessment
The assessment of policies and practices to prevent unauthorized access to private or public networks and network-accessible resources.
Database assessment
Used to identify vulnerabilities that might allow database-specific attacks like SQL and NoSQL injection, as well as general vulnerabilities and misconfigurations in a database server.
Application assessment
The identification of security vulnerabilities in web applications and their source code by using automated vulnerability scanning tools on the front-end or static/dynamic analysis of source code.
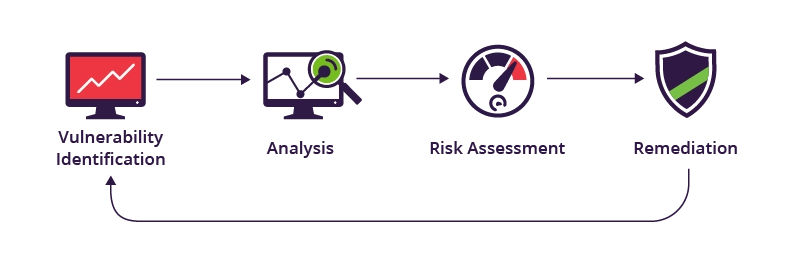
Vulnerability assessment process
Do you want to receive more information?
Fill out the form to be contacted as soon as possible by one of our consultants.


